Key Takeaways:
- Shop network security is critical in protecting sensitive manufacturing data from cyber threats, especially as more factories go digital.
- Implementing strong security measures, such as encryption and access controls, ensures data safety across IIoT systems.
- Regular updates and monitoring are essential to maintaining a secure and efficient manufacturing environment.
There’s been a lot of talk about the Industrial Internet of Things and security. Some scenarios can be very scary. Most of the threats would only be posed by a hacker who is specifically targeting your company and your data. Fortunately, that is not very common. Unlocking the potential of your machine data can bring mas sive productivity gains, and this usually outweighs these risks.
sive productivity gains, and this usually outweighs these risks.
First, there is a misconception that networking your equipment means that it’s immediately accessible on the public internet. In truth, even the most basic network connected to the internet places a router in front of the internet connection so any hacker from the outside would be unable to access the machines directly. However, this provision does not protect against vulnerabilities arising from unprotected software and sophisticated intrusions.
Follow these steps to protect your machines while they are being monitored:
1. Change all default passwords on routers and managed switches. You don’t want anyone on your network (a hacker or an employee) to be able to change your router’s settings. An unknowing employee or vendor could accidentally open up a security hole. A hacker who manages to get on your network could do a lot of damage with default passwords.
2. Use WPA wireless encryption. Never use a wireless network without encryption. However, WEP (wireless encryption protocol) is easy to hack. The newer alternative, WPA (Wi-Fi protected access), is difficult to hack. Even so, with the right tools and enough time, WPA encryption can be hacked. That’s why your most sensitive information should not be accessible from a wireless connection.
3. Ensure all PCs and servers are up to date. A PC that hasn’t had security updates to its software is much more vulnerable to phishing emails and viruses when opening unknown email attachments or running suspicious downloaded applications. Hackers often use these “zero-day exploits” to take control of a PC. Unless this is a targeted attack, a PC will likely be used as a spam email server, to find bank account details or to steal credit card numbers. If it is a targeted attack, the hacker could steal or modify sensitive company data that the compromised PC can access.
4. Buy a hardware firewall and keep it updated. There are many inexpensive hardware firewalls available on the market (SonicWall, Linksys,Cisco). Make sure the firewall is properly configured to receive daily security updates, which usually requires an annual subscription. Only one firewall is required, usually installed in front of switches connected to the public internet.
5. Enforce strong passwords. Make your employees use strong passwords for all of their accounts. Make sure that any cloud service enforces the use of strong passwords over HTTPS. Using children’s names, birthdays and other personal data makes a password easier to figure out.
6. Physically secure your facility. Being on site (inside the shop, that is) makes a hacker attack much easier. Keep doors locked, install a security alarm system, or take other precautions to stop intruders from accessing your physical network.
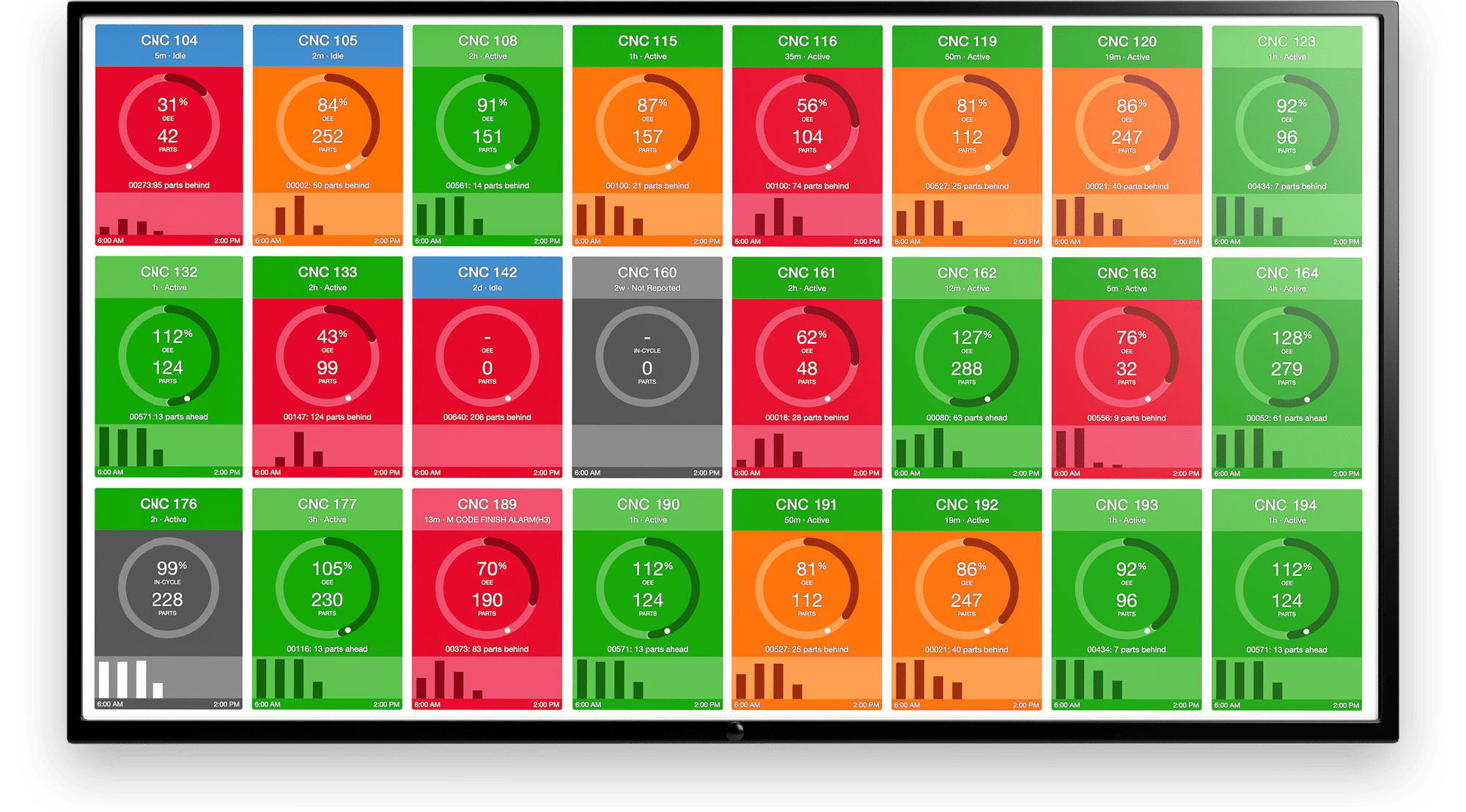
7. Put your CNC or other sensitive machines on a VLAN. A VLAN (virtual local area network) is an isolated network managed by a switch. You can lock down your equipment on a VLAN in way that is separate from your primary network. This prevents access to PLCs that run many machine tool subsystems. These controllers are often overlooked by IT, so the software is not updated very frequently. This software, especially if it is running an older version of Windows, is more susceptible to viruses and should never have open access to the internet. Your VLAN also should have no access to the public internet. A managed switch (available for around $500) will give you a very secure VLAN.
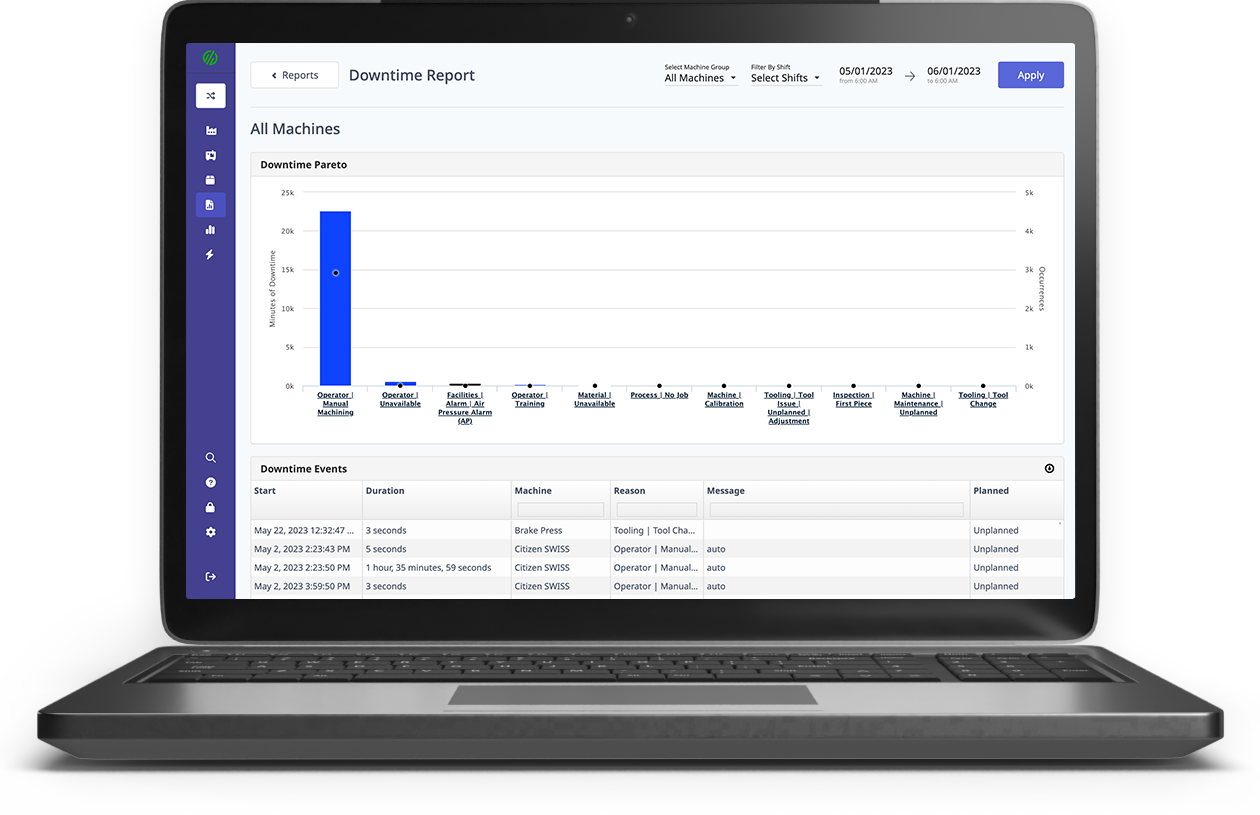
8. Manage connections to/from machines with a gateway. If the machine network is separate from the employee network, how does a machine-monitoring service have real-time access to machine data? This is achieved through a gateway, with two network interfaces, that acts just like a managed switch. One network interface communicates with the locked-down machine’s VLAN. The other network interface communicates only with the machine-monitoring service. This protects the machines from communicating, even indirectly, with anything but the monitoring service.
This article originally appeared in the June 2016 issue of Modern Machine Shop.
.png?width=1960&height=1300&name=01_comp_Downtime-%26-Quality_laptop%20(1).png)

 sive productivity gains, and this usually outweighs these risks.
sive productivity gains, and this usually outweighs these risks..gif)





Comments