The exponential growth of Industrial IoT is on track with recent predictions. And as we head toward a world with over 75 billion connected devices by 2025, almost a third will be utilized in industrial applications within manufacturing. But as the opportunities within this market - particularly in cloud-based, third-party service providers - continue to expand, one issue stands out less as a barrier to growth than it is a red flag not to be ignored. That red flag is the ever-present requirement of security.
With each passing week, there’s a new story covering breaches of data in much larger databases than before and at companies thought secure from such intrusions. Equally distressing are the cases where companies have stored or used the data collected in ways never intended by the people and businesses who entrusted them with the data to begin with. And with device proliferation gaining speed, the problem may get worse before it improves.
Within this article, we discuss common vulnerabilities for Industrial IoT networks as well as how you can address these vulnerabilities to ensure the safety of your network and business.
What is Industrial IoT?
The Industrial Internet of Things (IIoT) utilizes machine-to-machine connectivity and communication with a cloud-based platform to enable process improvement. It uses big data analytics, advanced machine learning algorithms, and other technology to deliver actionable insights to manufacturers.
IIoT represents the convergence of information technology (IT) and operational technology (OT), creating a fully integrated ecosphere where processes and industrial control systems are in a sophisticated network.
This network includes IIoT devices like sensors, controllers, industrial control systems, and other connected devices to measure production or assess machine health. Combined with edge computing and actionable insights generated from analytics, machines can receive instructions to perform autonomous or semi-autonomous tasks without the need for human intervention and at a speed more incredible than humans can achieve.
The Importance of Security for Industrial IoT
Industrial IoT security is critical. One primary consideration is the danger of business data loss. With more connections today than ever before, losing access to internal systems could seriously damage a company’s ability to do business or even survive.
The same is true for medical, aerospace, and defense industries, where patents, trade secrets, and regulated confidentiality require heightened accountability. The loss of ownership and use of these valuable intellectual assets could impact a company financially or put them in jeopardy of serious liability claims due to a breach of confidentiality.
Another critical consideration for Industrial IoT security is safety. There is an internal and external concern for IIoT for public and corporate safety. A security breach that allows outside access to devices could lead to injury or loss of life. And a violation that will enable the change of a formula in pharmaceuticals or a part performance characteristic in aerospace could extend the safety risk for many people outside the company.
How We Got Here
There are two basic reasons to explain how Industrial IoT arrived at this dilemma. One is based on simple math. With the number of deployed devices increasing exponentially, and pressure on service providers to get both the devices and the platforms out for deployment, the industry has been at risk of getting ahead of itself and doing more than security initiatives and protocols could absorb and respond to.
The second reason is an issue that has plagued other new and wildly successful technologies in the past. Namely, the issue of security had never had to be addressed at the machine level before. Therefore, no standards or protocols had been developed. In many ways this meant that providers either addressed them ad hoc as they encountered them, used the third-party security provider chosen by the client, or even relied solely on the client’s internal security measures (often inadequate in their own right).
Adding to the problem is that many service providers are slow or intermittent at deploying firmware upgrades as the push for new and improved core functionality often takes precedence. Regardless of how the problem has arisen, it’s one of the hottest issues in the industry today and one that many are struggling to address.
Locations of Security Concerns
As hackers become more sophisticated in the use of the same data tools and AI technology as those building out IoT systems, the risk of a data breach grows. Within a factory and its connected systems, there are a number of locations where a illegal access like a breach can occur:
- Insecure Web Interfaces: The location where users interface with IoT devices suffers from issues such as inadequate default passwords, lockout and session management issues and credential exposure within the network.
- Insecure Network Services: This is where hackers may be able to gain access to the network itself as through open ports, buffer overflows and Denial-of Service attacks.
- Weak Encryption: Weak encryption, or in some cases no encryption, can allow intruders the ability to gather data during the exchange between devices.
- Insecure Mobile Interfaces: As many companies offer field service as an extension of their manufacturing operation for repair and maintenance, mobile interfaces suffer from the same issue of encryption and authentication.

The Challenges of IIoT Security
Many businesses already have weak or improper security in place to begin with, which places a strain on IoT providers supplying both services and devices. More than 50% of all critical infrastructure operations utilize outdated Microsoft software and a full 40% of all industrial sites are using the public internet.
This puts machine infiltration as a key risk as IIoT devices proliferate, meaning that sophisticated hackers could conceivably secure remote access to an entire factory and either severely disrupt or damage the production capabilities for a lengthy period. Security vulnerabilities could also pose physically dangerous conditions as a direct or indirect result of an intrusion.
The security of legacy systems is also a concern. One of the key value propositions for Industrial IoT deployment is that legacy equipment and legacy devices can be retrofitted with IoT devices. This allows longer equipment lifecycles and full integration for building out a smart factory without triggering expensive capital equipment purchases. But the choice must be made alongside a careful consideration of which devices can be properly secured for use within the system, a skillset that a company may not have and one it may not realize it needs.
Lack of standards and protocols in an industry still in its infancy, but growing astronomically, are also hampering coherent IIoT security progress. The feeling is that IoT service providers as a business community and industrial organizations will come together and self-regulate to develop standards and protocols for all development and to mitigate any security risk.
This would eliminate the chance of competing or overlapping “local” protocols and would be most cost-effective for the client. Until then, the lack of standard makes ad hoc security a norm and stresses the capabilities of the client’s existing security system, which may already have its own weaknesses.
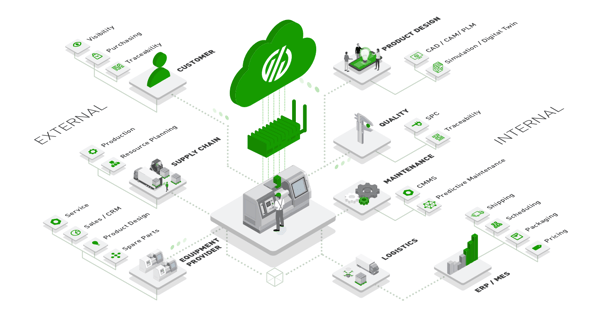
Industrial IoT Security Solutions
According to security experts, over 40% of all breaches consist of either malware or brute force attacks. But there are numerous other forms of intrusion as well. Because of the number of ways a company’s devices and systems could be accessed, security is viewed as consisting of four tiers; device, communication, cloud, and lifecycle management. Because of the speed at which the industry has grown, this complicates security solutions as there is no end-to-end, out-of-the-box security solution.
But there are steps that can be taken by providers and companies in the interim as end-to-end solutions are developed.
One such step would be to segment the IT network so that anything that controls equipment is maintained in a separate network from the rest of a company’s IT infrastructure. These distributed control systems would route network traffic over multiple channels and achieve security by decentralizing the network to protect industrial settings.
A second step that service providers can take is to ensure the “basics” like secure network communications. Basic structures such as credential lockout after a small number of tries and default credentials that must be changed upon activation will help secure access at the web interface. Likewise, mandating strong password rules and two factor authentication can limit unauthorized access.
At the IT level, making sure that services aren’t vulnerable to buffer overflow and ports are closed when not used will shut off avenues of intrusion as well. The same precautions can be built into mobile device interfaces for password, lockout and default password rules. And of course, better discipline in producing and deploying firmware upgrades will help reduce system degradation.
Perhaps the biggest step that could be undertaken to get ahead of security risks would be for the industry to collaborate toward self-regulation in the development of industry standards and protocols. By defining a base architecture for many of the issues above and standardizing and mandating their inclusion, service providers and their programming teams would be freed from the smaller security concerns and left to concentrate on larger and more intensive security issues as they evolve.
The setting of basic standards would put a minimum security “floor” under all systems to protect both the companies that purchase the services as well as the providers when deploying systems in companies with inadequate or weak security systems.
Security Challenges will Continue to Grow with IoT
The security challenges facing Industrial IoT service providers and their client companies are growing. Many don’t emphasize the security side of the equation strongly, but by not doing so, opportunity is missed. Many executives have indicated that they would be willing to pay more for IoT devices and services if security solutions were part of the package. But as the industry continues to grow, new services including security as part of the platform, or strong partnerships with third-party security providers, will gain a stronger footing in the market.

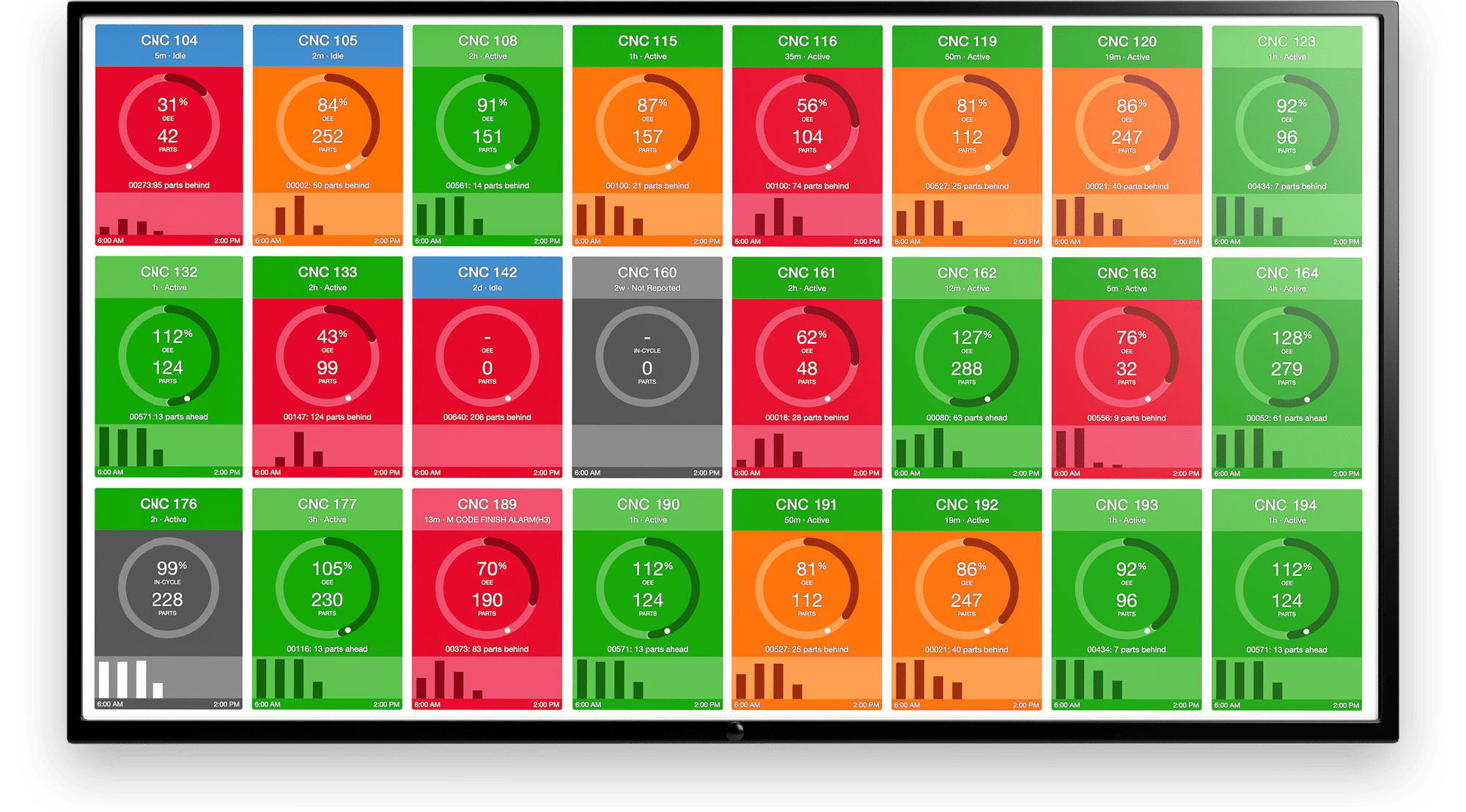
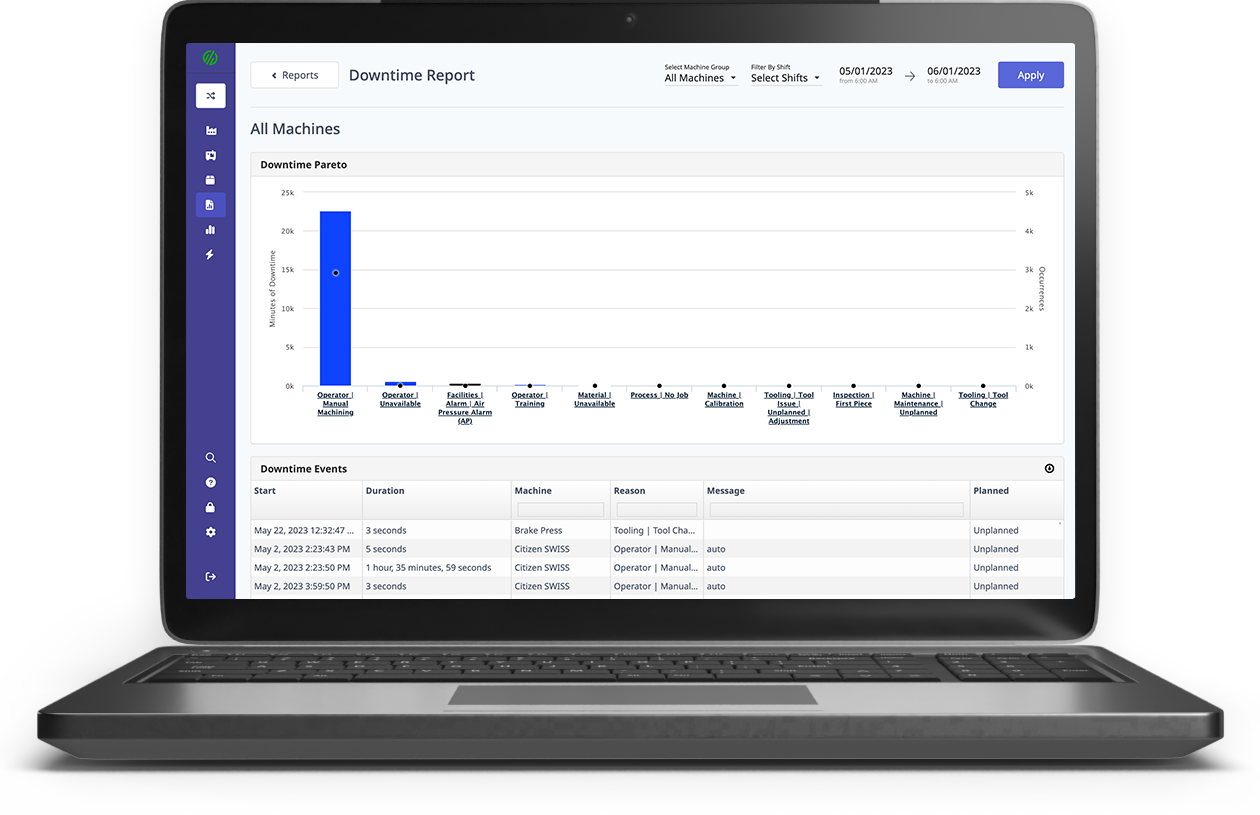
.png?width=1960&height=1300&name=01_comp_Downtime-%26-Quality_laptop%20(1).png)




.gif)





Comments